Solutions
Email Filtering
The problem many executives face is figuring out how to filter out spam without losing legitimate emails, and doing it all for a cost-effective price. We have your answer: Spamhaus and SURBL BV. The industry’s leading Real Time BlockLists ( RBL’s ), with the highest block rates and lowest false positives. Greatly improve your effectiveness, block rates and accuracy.
Spamhaus and SURBL BV Considered to be Best Practices Approach to Fighting Spam.
The use of Spamhaus, the #1 anti-spam block list, and SURBL BV, a leading domain blocklist, are considered best practices when it comes to email filtering services and fighting spam.
Two-Stage Filtering
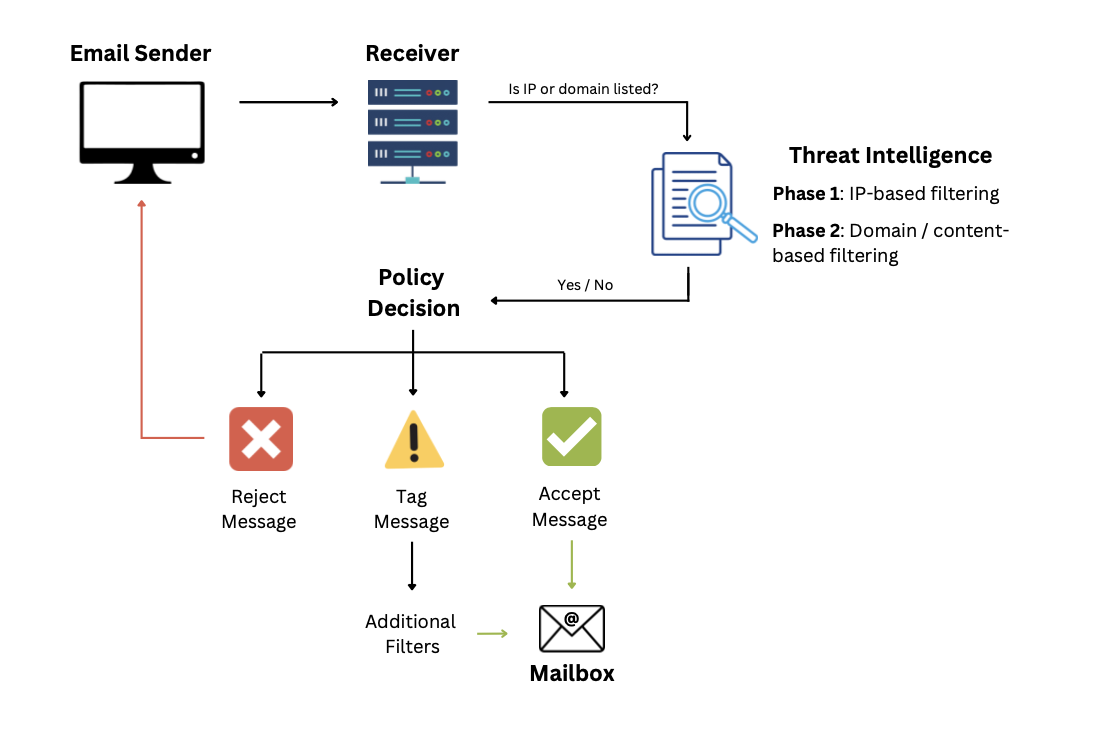
Phase 1: IP-Based Email Filtering
The first stage of email filtering looks at the sender’s IP address. Real-time threat intelligence feeds are used in this first stage to identify and block known malicious IP addresses. If the email sender’s IP address is included in threat intelligence blocklist, the policy decision will tag or reject the message.
Using IP blocklists, like the ones below from Spamhaus, stops known malicious IP addresses from sending messages to email users. IP blocklists are the most effective first line of defense against spam, botnets, malware, ransomware, and more. Spamhaus offers the #1 anti-spam IP blocklists, blocking up to 95% of spam messages with <0.02% false positives.
Spamhaus Blocklist (SBL)
IP addresses have been involved in spam or controlled by known spammers
Spamhaus Blocklist (SBL)
IP addresses have been involved in spam or controlled by known spammers
Exploits Blocklist (XBL)
IP addresses of virus-compromised computers that are sending spam
Exploits Blocklist (XBL)
IP addresses of virus-compromised computers that are sending spam
Policy Blocklist (PBL)
IP addresses that not be delivering unauthenticated SMTP email
Phase 2: Domain and Content-Based Filtering
The second phase of email filtering checks domains and content contained in the body of the email message.
Email filters check these domains against domain / content-based threat intelligence feeds. Domains included in the blocklist are known to be involved in malware, phishing, spam and other cyber threats.
Domain-based blocklists identifies what type of cyberthreat the domain is involved in when the mail server or spam filter queries it, allowing policy decision to reject, tag or accept the message.
Ongoing Innovation: Latest techniques also allow email filters to block based on email content / hashes. Hash blocklists are new effective method at identifying and filtering cryptocurrency addresses, malware files, email addresses. Hash blocklists are also used to block malicious domains hiding behind re-directors or shortened URLs, often missed by IP- or domain-based blocklists.
Content based threat intelligence feeds from Spamhaus and SURBL BV.
Spamhaus Domain Blocklist (DBL)
List of spam domains that link to fraud, phishing, and malware sites.
Spamhaus Domain Blocklist (DBL)
List of spam domains that link to fraud, phishing, and malware sites.
Spamhaus Zero Reputation Domain
Newly-registered and previously dormant domains added to this block list for 24 hours.
Spamhaus Zero Reputation Domain
Newly-registered and previously dormant domains added to this block list for 24 hours.
Spamhaus HASH BL
List of hashes observed in malicious activity, as opposed to IP addresses or domains.
Spamhaus HASH BL
List of hashes observed in malicious activity, as opposed to IP addresses or domains.
Multi
Domains observed to be engaging in or connected to phishing and botnet activity, as well as cracked and abused domain.
SURBL Multi
Domains observed to be engaging in or connected to phishing and botnet activity, as well as cracked and abused domain.
Fresh
Data feed identifies newly registered domains before they can establish their domain reputation.
SURBL Fresh
SURBL’s Fresh data feed identifies newly registered domains before they can establish their domain reputation.
SURBL BV Shortener / Hash BL
Feed to identify malicious email content and domains hiding behind URL shorteners and redirectors.
SURBL Shortener / Hash BL
NEW feed from SURBL identifies malicious email content and domains hiding behind URL shorteners and redirectors.
Email Filtering Blocklists provide:
The world’s best IP and domain anti-spam filters
Ongoing Innovations: Continuous enhancements in Email Blocklists, CrytoWallet, Shorteners, and more.
Highly-accurate blocklists with near zero false positives. The most effective and accurate data
Enhanced protections from spam, phishing, malware, ransomware, and more
The best financial and technical approach
Full licensing and support
SecurityZones is Your Email Security Partner
SecurityZones is the leading global distributor and technical expert for both Spamhaus and SURBL BV. We serve as an extension of Spamhaus and SURBL BV technical and R&D teams, and provide users with more than a decade of experience. SecurityZones works directly with the leading ISPs, security vendors, universities, and enterprises to deliver cutting-edge data feeds, threat intelligence, and technical support. When you work with us, you not only get access to the best anti-spam data, you also get:
- Improved coverage and effectiveness of email filtering
- Lifetime partnership approach
- On-going meetings and consultation, to provide you with insight on new feeds, features, and techniques
- Consultations on how to best use the data to address your objectives and improve your products and services
Start your free trial.
Design the best set of data feeds to meet your needs!
Experience improved cybersecurity and stop phishing emails, ransomware, malware, and other cyber threats. Sign up for your free consultation and receive an in-depth technical deep dive and a 30-day free trial.



