Spamhaus
Passive DNS
"Shining some light on the darker side of the internet."
Passive DNS is a technique in which sensors capture inter-server DNS messages and forward them to a collection point for analysis. After being analyzed, individual DNS records are stored in a database where they can be indexed and queried.
Spamhaus operates its own passive DNS sensor network, collecting this anonymized DNS query data from thousands of recursive DNS servers around the world. As a result, Spamhaus creates passive DNS datasets of domains that are or have been directly associated with cybercrime.
Passive DNS historical databases can be used to answer questions that are difficult or impossible to answer with other security tools including:
- Where has this domain name pointed to in the past?
- What domain names are hosted by a given name server?
- What domain names point into a given IP network?
- Uncover the ‘IP footprint’ of an attacker: See if attackers can still access to your IT Environment/ Track and correlate log data to see what was accessed.
- Identify use / misuse of brands and keywords across cyberspace
- Identify your organizations assets that are exposed to the Internet
Spamhaus
Passive DNS
Improve your visibility and investigation of cyberthreats.
Passive DNS gives security analysts a tool to connect the dots and uncover more malicious activity on their network faster and more accurately.
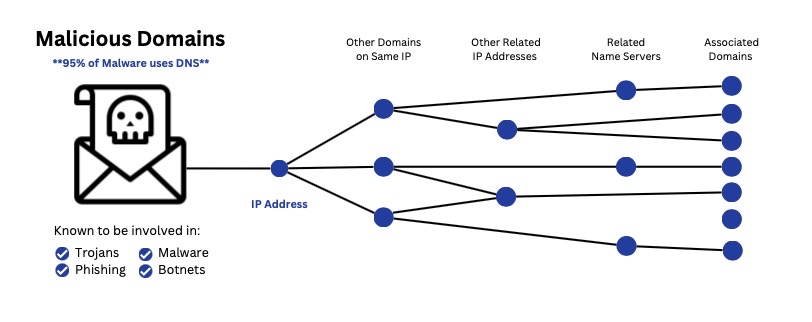
As crime has moved online, cybercriminals have begun to rely on DNS to build their malicious infrastructure. Now, cybercriminals use domain names, IP addresses, name servers, and other DNS assets to commit crimes. By uncovering relationships among DNS assets, such as determining which cybercriminals are using the same IP address for different campaigns, we gain new threat intelligence about the type, scope, and breadth of the crime. We can even find out the attribution.
Key Features & Benefits: Passive DNS Service
Massive, Historical Database: BILLIONS of unique records for tracking and linking domain names to particular name servers and IP networks.
Proactive Security: Identify and protect against potential threats and malicious networks. Passive DNS exposes the links between name servers and domain and helps to identify new malicious domains as soon as they go live.
Accelerate Investigations: Intelligence for incident research and post-breach analysis, including type of crime, the scope breadth of campaign and even attribution. Passive DNS data for context, enrichment and correlation to aid investigations.
Brand Monitoring: Monitor any use or misuse of brands in cyberspace. Keyword and fuzzy search of DNS database.
Network Auditing: Identify hosts and assets advertised on the internet. See any IT infrastructure exposed publicly. Passive DNS also provides enhanced visibility to subnets, DNS records, and Network footprint.
Flexible Deployment Options: Spamhaus Passive DNS is available via web portal, API, or ‘on the wire’. Choose the method that works best for your team.
Privacy Protection: Passive DNS data does not contain any personally identifiable data (PII) for privacy right and GDPR compliance.
People who use Passive DNS
Security Professionals can use Passive DNS to investigate domains or IP addresses that have raised suspicion, and find out if it is a single malicious IP or a complex multi-layered operation they are dealing with. They can:
- Investigate domains that are within the same subnet of a particular IP address – some (or most) of these may display similar behaviors like the one that has caused you concern.
- Abusers recycle their resources e.g. the same web server may host several phishing domains, not just one. With Passive DNS you can acquire the information before, or as soon as they change their domain or IP address.
- If you are dealing with a more complex operation, the abuser may have the full /24 subnet under his control and Passive DNS can potentially provide additional, deeper insights e.g. all the domains that are pointing to an IP address in the subnet,
- Learn attackers IP’s/footprint (what else belongs to them) and see if they still have access to your IT environment by tracking and correlating with log data to see what was accessed.
Passive DNS searches will also permit you to find invalid or unauthorized records in the zones you control, caused by unauthorized access or by cache poisoning/spoofing (where corrupt DNS data is introduced into the DNS resolver’s cache, causing the name server to return an incorrect result).
Passive DNS can ease the burden on Malware Researchers by reducing the need for complex reverse engineering when dealing with malware.
Once you have an IP address for a Botnet Command & Control (Botnet C&C) Server Passive DNS enables you to drill down and analyze the host names served by the same IP address and extend your searches, for example, to the authoritative name servers for the domain.
Passive DNS has the potential to assist various IT security roles, including Penetration Testers. Take a look at the highlights below to get a clear understanding of how Passive DNS can provide you with deeper insights into the security of the networks you are evaluating.
Search for all the DNS records relating to the subnets of the domain you are investigating, to highlight what different functions the servers are being used for. Things to look out for:
- A host named “firewall.yourcustomerdomain.com” suggests a high likelihood that this is the firewall, allowing you to select the relevant testing tools you should be used on this type of domain.
- A host named “webdevel.anothersite.com” is likely to be a domain where development is run from and could yield some interesting penetration results.
- Look for any IP addresses running live versions of outdated software – this has the potential to increase the attack surface.
- See the IT Infrastructure that is exposed to the Internet – can very easily (in seconds) understand what resources are exposed and advertised on the Internet
Using the information gathered in the above steps, you may uncover subnets exist as part of the infrastructure, which you weren’t aware of but are of interest to you. Use Passive DNS to drill down into the newly discovered networks.
Passive DNS adds value to multiple roles, including Brand Protection Specialists. You can utilize Passive DNS to highlight shadow domains, or typosquatting and identify who is masquerading as your company, brand or trademark and potentially hurting your customers and damaging your brand.
Search the Passive DNS database for domain names that contain the whole name of your company, or a specific key word.
- Pinpoint malicious domains and easily view their IP address.
- Search this IP address to uncover any further domains this address that may have been connected with historically.
- Use Fuzzy Search to discover misspelled, and close matches to brands and keywords
- Internationalized Domains – able to identify IDN’s which appear to be your brand/keyword
For additional intelligence subscribe to our real-time zero reputation domain zone (ZRD), and view all domains which have been registered within the past 24 hours (which have a higher likelihood of being used for fraud)
How To Use Passive DNS
Passive DNS Dataset Deployment Options
Web portal: Web portals are designed for information security professionals and cyber incident response teams that want to conduct digital forensics. Web portals are also for security researchers who want to investigate what kind of activity is associated with particular IP ranges or analyze the relationships between DNS queries and responses.
API: API is for security vendors and SOC/SIEM teams who want to offer passive DNS as a service and integrate the raw datasets with their own software and security platforms.
Continuous Data Feeds: Continuous feeds ‘on the wire’ is for security researchers, companies and law enforcement agencies who need to continuously observe live, recursive DNS traffic to help in the identification of new malicious domains, emerging threats, and cybercriminal trends.
Start your free trial.
Design the best set of data feeds to meet your needs!
Experience improved cybersecurity and stop phishing emails, ransomware, malware, and other cyber threats. Sign up for your free consultation and receive an in-depth technical deep dive and a 30-day free trial.



