Spamhaus
*New* Spamhaus Hash Blocklist (HBL)
Spamhaus Hash Blocklist (HBL) can help protect system’s with cryptographic hashes that have been involved with malicious activity. Blocking based on hashes allows for more precise blocking than IP addresses or domains. Some domains or IP addresses, like Gmail or Yahoo, are too large to be listed by traditional IP- or domain-based block lists. Now, emails can be analyzed and filtered based on content (hashes) to protect against fraudulent activity.
Content detected by the Hash Blocklist includes:
- Email addresses ( compromised accounts from gmail, yahoo, etc )
- Cryptocurrency addresses (known crypto wallets, used in maliciosou activities )
- Malware files
Hash Blocklist is included in the Spamhaus Content Blocklist subscription, via Data Query Service or Spamhaus Intelligence API.
How does a Malware Hash Blocklist work
Spamhaus HBL will provide return codes signally:
- Hashes are malicious: The file queried been analyzed by Spamhaus Malware Labs and is known malware. The Block List will also return the malware family.
- Hashes are suspicious: The file queried has been associated with spam and is suspicious. The file has not been confirmed to be malicious by Spamhaus Malware Labs, but the file should be treated very cautiously.
Spamhaus
Hash Blocklist: Key Features & Benefits
Enhanced Protection: Block emails from compromised accounts at large ESP/ISPs (e.g. Gmail, Yahoo, etc.) that aren’t included in traditional IP- and content-based block lists. Approx. 1.1 million listings on average.
Real-time Updates: As soon as researchers observer and list the threat, users are protected. Malware Hash BL can list and block malware hashes within 30 seconds of observation.
Near-Zero False Positives: Spamhaus data feeds have <0.02% false positives. Highly accurate data ensures legitimate traffic can be sent and received.
Expertly Research Data: Spamhaus has 23 years of experience identifying cyber threats. Over 13.4 Billion global SMTP connections, 1.5 million IPs, 3 million domains analyzed daily.
Simple Integration: Using traditional DNS queries or Restful APIs ensures easy configuration. Data feeds can easily be added to your existing mail filtering systems.
Delivery Options: HashBL is available via Data Query Service or Spamhaus Intelligence API. Choose the method that works best for your team.
Reduce Processing & Storage Costs: Blocking threats before they can enter a network to free up bandwidth and server space.
Minimize Risk: Save time and costs related to security incidents,
Privacy Protection: Data is hashed to eliminate any personally identifiable information (PII).
Spamhaus
How does a Cryptowallet Hash Blocklist work?
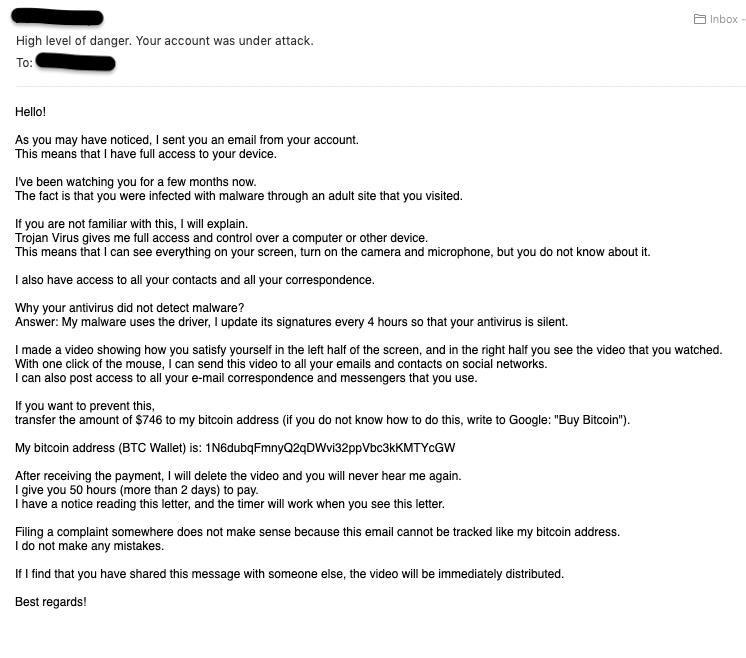
Below is an example of a commonly-seen “sextortion” scam email. The email includes a bitcoin address to trick victims into making a payment. Malicious emails sent from a reputable IP or domain can evade filtering. However, the bitcoin address can now be used to assess the nature of the email and flag malicious content. Even if the sending email doesn’t trigger a rejection based on IP or domain reputation, the bitcoin address can be used to determine that the email is malicious in nature and result in the email being blocked anyway.
This blocklist is included in a Spamhaus Content Blocklist subscription. The data feed is available via our Data Query Service (DQS) or the Spamhaus Intelligence API.